Cyber security analysis and control of complex cyber physical systems based on opacity
As the basis of this project, Ji’s group has done systematic research on cyber security, optimization and control of cyber physical systems (CPS). A series of novel results have been achieved on topics including security protection, supervisory control and performance optimization. To be more specific, in order to mitigate the security threats, an information flow based security protection framework has been proposed, which includes obfuscation based opacity enforcement by edit functions and quantitative edit function synthesis under energy constraints. To mitigate the complexity burden of synthesis, compositional and modular edit function synthesis methods are developed, with improved scalability. In addition, quantitative supervisory control of discrete event systems has also been investigated to optimize the performance of cyber physical systems. Game theoretic supervisor synthesis techniques are proposed to solve the optimal asymptotic mean payoff supervisory control under partial observation and rolling horizon mean payoff supervisory control problems, respectively.
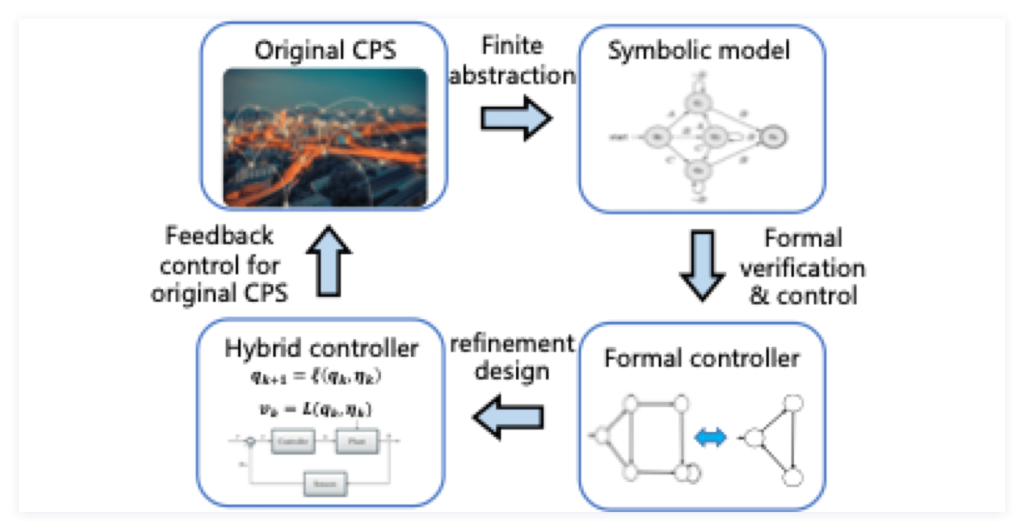
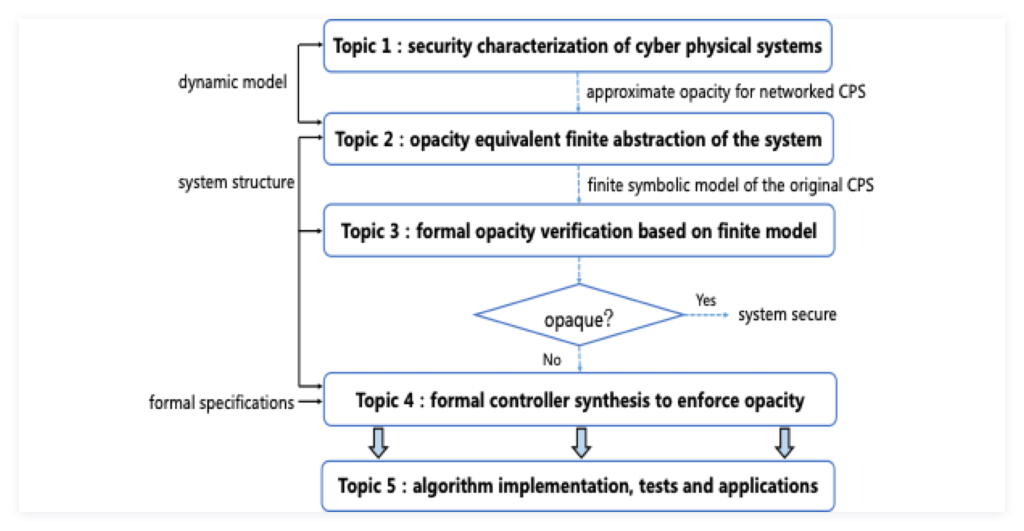
Based on the above results, this project aims to tackle the challenge of security protection of CPS against outside malicious attacks. Given that the system under consideration is high dimensional, heterogenous in nature, and may suffer from signal delay and loss in sensor and actuator channels, a systematic formal information security analysis and control framework will be proposed which is centric on opacity of networked control systems. Specifically, this project includes the following topics. First, we propose the concept of approximate opacity under the setting of networked control systems to characterize the cyber security properties under attacks, which bridges the gap between the heterogeneous cyber layer and physical layer of the system, as well as considers the potential command delay and loss of the communication channels. Second, a finite approximation method is investigated to reduce the state space of the system model and guarantees that the model before and after abstraction are equivalent in terms of opacity. Third, a formal verification scheme is considered to determine whether the system remains to be opaque under the given cyber attacks. In addition, a secure-by-construction supervisory synthesis method is proposed if the given system is verified to be not opaque, which guarantees that the closed loop system satisfies opacity. Finally, the above proposed theoretical algorithms will be implemented to develop a software tool. Then tests and experiments will be performed on robotics and autonomous systems platforms, especially for task planning and control scenarios. The overall research idea of the project is summarized in Figure 1 and the major research topics are shown in Figure 2.